
Ugloo offers indestructible storage:
resilient, multi-site, encrypted, decentralized and immutable.
Data encryption
Ugloo implements state-of-the-art data encryption.
Transit encrpytion
- Connexion TLS connection between client and
S3gateway.- using self-signed certificate or one delivered by the customer.
At-rest and cluster-wide transit encryptions
Data is encrypted when its written in the cluster.
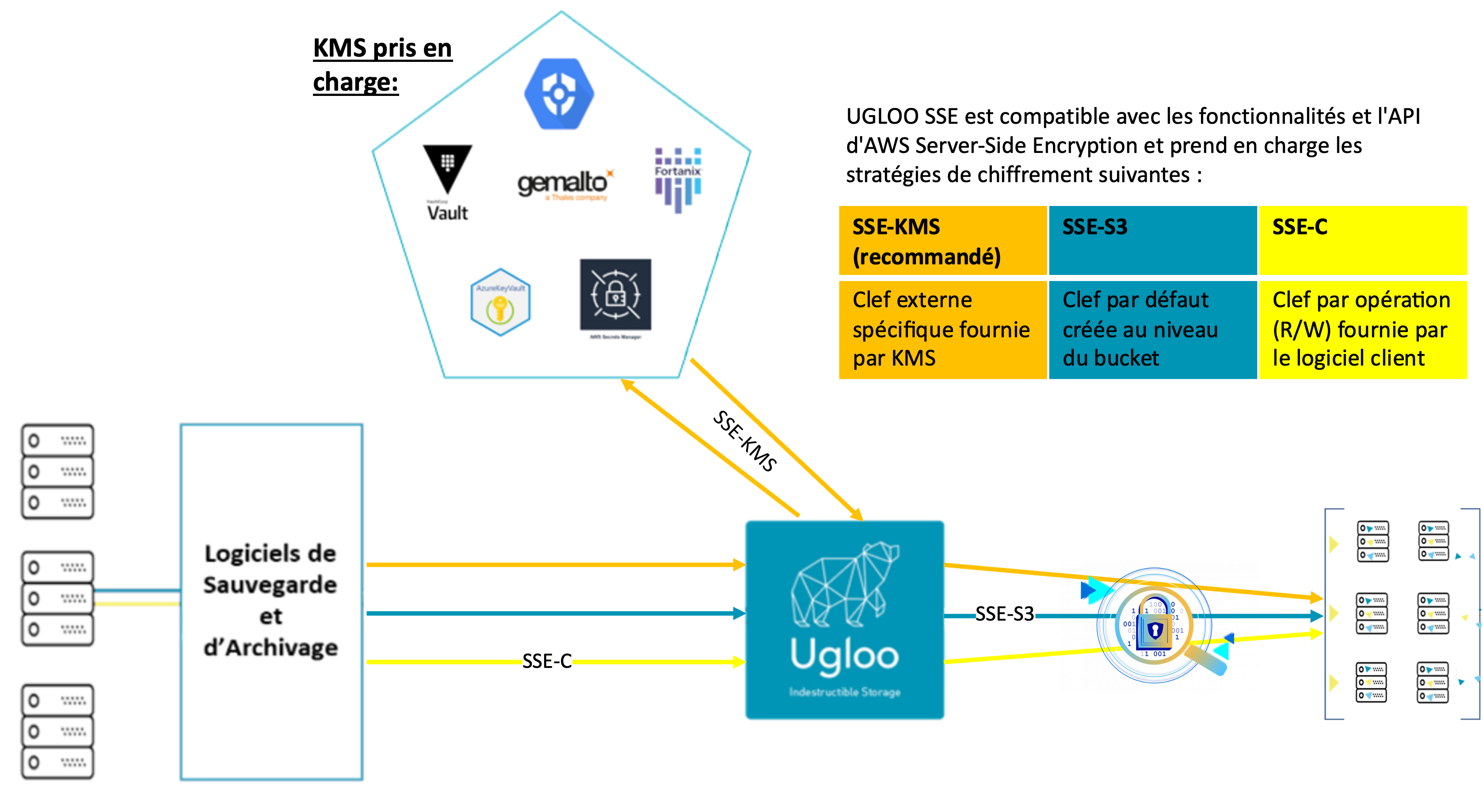
UGLOO SSE is compatible with AWS Server-Side Encryption features and API and supports the following encryption policies:
SSE-KMS, where the dedicated key is delivered by a KMS- internal PKI is available in your
Ugloocluster - you may use your favorite external Key Management System
- HashiCorp Vault
- Azure Key Vault, AWS Key Secure Manager, Google Cloud KMS
- Fortanix Data Security Manager
- Gemalto SafeNet KeySecure
- internal PKI is available in your
SSE-S3, where a default key is generated for encryption in each bucketSSE-SC, where a key is delivered by the customer for each and every operations on an object (erad/write).
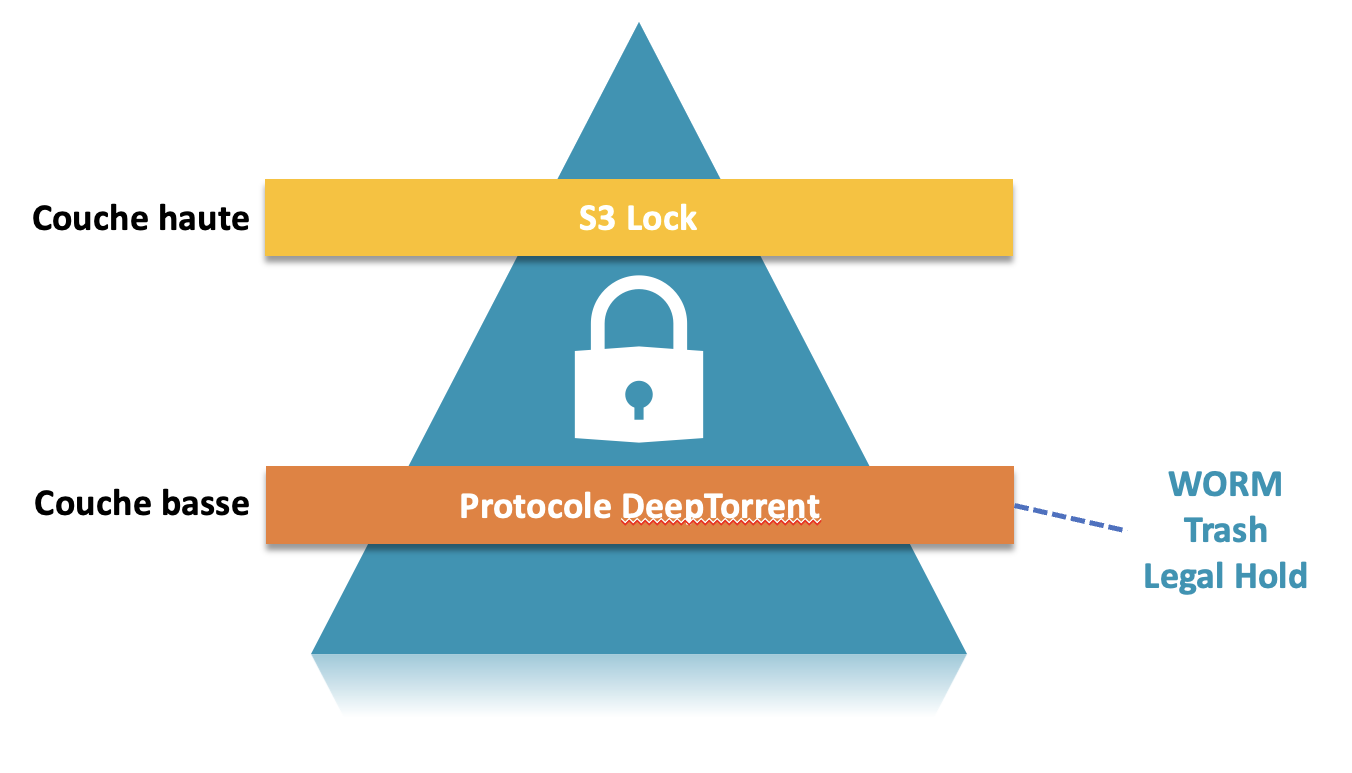
Double immutability
Cryptolocking ransomware is no match for the data stored in Ugloo. Each version of an object has double immutability:
- at the
S3object configuration level through the lock modes and the retention periods. - at the
DeepTorrentfragments level, which are natively immutable- with configurable regulatory retention period
- and recoverable trash
Security audit on BitTorrent protocol
Ugloo relies on libtorrent open source library. Onto which a security audit has been performed at the end of 2020, ordered by Mozilla Open Source Support Awards et performed by include security.
